APPENDIX C – SCENARIO
C.1. Scenario Design
In the scenario, the ACI wanted to (1) introduce effects that caused catastrophic damage on a single entity or organization; (2) have those effects spill over into another sector; and (3) eventually have the catastrophic effects reach multiple entities and organizations. This strategy allowed the ACI to examine the interdependencies and incident response gaps of the various critical infrastructure organizations participating in the experiment. Figure 17 is an illustration of the ACI’s scenario development framework.

Figure 17: JV 3.0 Scenario Development Framework
C.2. Scene Setter
For several days, heavier than normal spring rains have inundated the southeastern area of the Appalachian Plateau, causing widespread flooding in the area and regions to the south and east. Rivers are overflowing, resulting in over 44,000 being displaced in northern GA and western SC. Rivers are anticipated to remain high for the next several days. The governors of GA and SC have deployed the National Guard to their respective regions for humanitarian relief and the protection of infrastructure.
Meanwhile, the President of the United States has ordered the immediate and rapid deployment of two brigade combat teams to Europe to respond to aggressive actions taken by a geopolitical adversary of the United States. Within the international community, the civil conflict is largely viewed as a proxy war, with several ethnic factions opining publicly that foreign powers should stay out of the internal conflict. The local and global media are heavily covering the international dialogue, and several major powers with interests in the region would benefit from the United States remaining uninvolved. The U.S. secretary of state and secretary of defense have conducted a joint press conference, stating that the United States will rapidly deploy forces to the region to protect regional interests. In addition to combat troops, the President has ordered the deployment of defense systems, including vehicles, radars, missile systems, and other equipment, to support U.S. allies abroad.
Several Army battalions have been placed on alert for movement, and the forts and local community are aware that personnel and equipment are being deployed. The Army (Military Surface Deployment and Distribution Command [SDDC]) begins coordination activities to move vehicles and equipment from the local forts to the ports in Charleston, SC, and Savannah, GA. Most community residents know that troop and equipment movement is scheduled for September 22–24, 2020, though that is sensitive information. To support the summer offensive, the United States must have support to its allies by November 1, which necessitates departure from the United States by September 30 at the latest. Local news media has widely covered the local impact to communities because of the rapid deployment’s large scale. Several activist groups have voiced strong opposition to the United States deploying troops to the region.
In addition, recently, DHS CISA released a preliminary alert that a new version of Emotet has been detected that indicates it can propagate via wireless networks. USCG has issued a maritime alert warning shippers, ports, and maritime facilities that the most recent version of Emotet malware is contaminating ships and maritime facilities globally, with over 43 new infections being discovered in vessels and port facilities. Within the past 6 months, U.S.-flagged vessels have been delayed entry into port four times because of widespread Emotet infections on their noncritical information systems. A Joint Intelligence Bulletin from DHS and the FBI highlighted disruptive ransomware attacks targeting the energy industry as an emerging concern.

Figure 18: Domestic Terror Group Threat on Social Media
Furthermore, within the energy and utility sectors, Ryuk ransomware is being discussed often, and specific malware such as CrashOverRide and Triton continue to be of interest.
C.3. Turns 1–3 (ROC Drills and Preplay)
C.3.1. Turn 1
In turn 1 (Monday at 8 a.m.), the SDDC rapid deployment process has begun. The crews of several commercial cargo vessels report manifest system glitches. The main gate at the port terminal fails to open roughly once in every 20 attempts. As a solution, port security manually opens the gate, positioning additional personnel to do so. Meanwhile, electricity and natural gas utilities are experiencing phishing attempts. The FBI has issued a Private Industry Notification about advanced persistent threats targeting the energy sector. In addition, the media is reporting that protests against U.S. involvement overseas will most likely be happening at the military terminal. Furthermore, domestic terror groups have threatened to derail SDDC’s operations by posting a picture of a derailed train on social media.

Figure 19: Media Coverage of the Protest at the Military Terminal
C.3.2. Turn 2
In turn 2 (Monday at 5:47 p.m.), the public safety answering point is reporting a high volume of 911 ghosting calls. The electronic manifests of ship and rail cargo are being reported as inaccurate. Spam emails are being sent from SDDC email addresses. An energy security operations center has noted an uptick in suspicious emails and admitted that multiple employees in the human resources department have clicked on phishing links. In addition, a wireless router was discovered to have been installed in a traffic box. Port facilities are experiencing power voltage and quality fluctuations. Furthermore, the FBI has deemed the threats on social media from domestic terror groups as credible. Also, protests have begun at the military terminal, with the students and faculty of local high schools and colleges making up a large portion of the crowd.
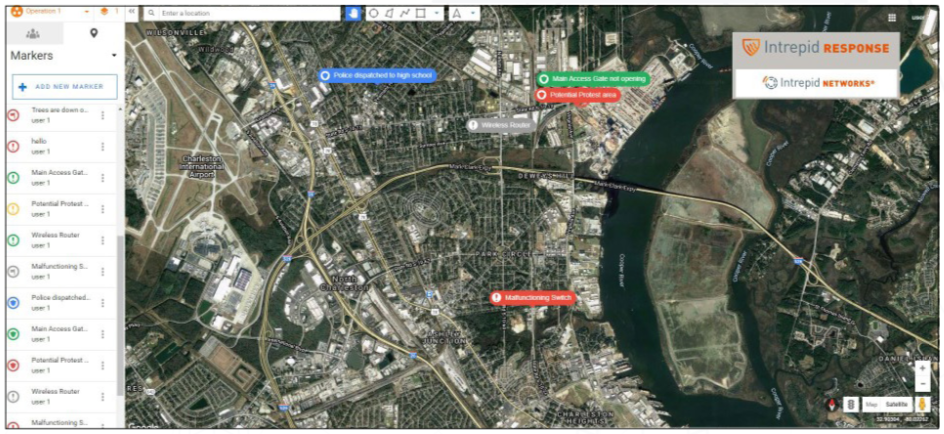
Figure 20: Turns 1–3 Common Operating Picture (Charleston)
C.3.3. Turn 3
In turn 3 (Tuesday at 7:21 a.m.), 911 call centers are struggling to manage incoming calls because the 911 ghosting has become overwhelming. The electronic manifests of ship and rail cargo are still inaccurate, and the port database has been discovered to be corrupted as well. In addition, the access database for entry into the port has been corrupted; as a result, the backup system has been implemented. The spam emails from SDDC email addresses are increasing in volume. The malware Emotet has been detected on ships heading for the port, and the FBI has confirmed two of these cases. Furthermore, a malfunction has occurred at a major rail switching station. Also, Department of Transportation crews are investigating instances of possible sign and light tampering, but the crews have come to no conclusions yet.
C.4. Turns 4–7 (JV 3.0 Exercise Main Play)

Figure 21: Trucks Entering the City Are Backed Up on the Highway
C.4.1. Turn 4
In turn 4 (Tuesday at 3:42 p.m.), the discovery has been made that natural gas utility remote terminal unit firmware does not match the latest patch from the vendor. The energy information sharing and analysis center has issued a traffic light protocol of “AMBER” because of credible cyber threats. Port and local law enforcement are coordinating to monitor the protests. Protesters are livestreaming, and the protests have garnered international media attention. Emails purportedly from the Port Authority are sending past-due invoice emails to electricity utility employees. Electricity and natural gas utilities are worried that their automated pay systems will fail to pay employees on payday. In addition, SDDC’s Integrated Computerized Deployment System (ICODES) is suffering from constant glitches. A power plant night-shift manager believes his cursor was moving by itself. Port properties are experiencing vandalism, including graffiti and broken windows. Furthermore, the denial-of-service attack is ongoing at the 911 call center. Also, traffic is becoming a problem; with lights and signs being manipulated, trucks attempting to enter the city are backed up on streets and highways.
C.4.2. Turn 5
In turn 5 (Tuesday 10:58 p.m.), a major voltage drop has occurred at an electricity distribution substation serving the city, and three natural gas compression stations serving the city have experienced depressurization. Loss in pressure has led to a drop in electrical output at the power plant, which has activated backup fuel reserves. Elsewhere, the local police department is now experiencing ghosting calls. Media are flooding the mayor’s office, seeking information and comment. In addition, a freight truck has lost control and crashed into multiple vehicles on I-95, causing a massive backup in traffic. Traffic is being diverted off the interstate.

Figure 22: Turn 5 Common Operating Picture (Savannah)
C.4.3. Turn 6
In turn 6 (Wednesday at 8:14 a.m.), a ship has listed (i.e., tilted) and dumped 52 cargo containers (not including military equipment) onto the pier and into the adjacent water. The port has closed pending an investigation into the cause of the malfunction; investigators are attempting to ascertain if hazardous materials were in the containers. Meanwhile, ICODES is completely nonfunctional. Two more freight trucks have stalled, this time in city intersections; the drivers are reporting that their engines “just shut off.” Two protective relays at relay stations servicing the port and the local hospital have taken uncommanded actions; apparently, this was the result of a sensor failure. In addition, the security operations center has discovered indicators of compromise on utilities’ OT systems.
C.4.4. Turn 7
In turn 7 (Wednesday at 6:10 p.m.), USCG and the Port Authority are still investigating the reason the cargo ship listed. With port access closed, rail, freight, and shipping have been severely impacted. In addition, a water treatment plant has experienced power failure, and the local school district has no running water as a result. Backup power at the port has been inconsistent. The energy utility has confirmed that its human resources system has been infected with Ryuk malware ushered in by Emotet. Furthermore, the city traffic system has been hit with ransomware that appears to be localized to the city traffic network.

Figure 23: Turn 7 Common Operating Picture (Charleston)
Table of Contents
- 1. FOREWORD
- 2. ACKNOWLEDGMENTS
- 3. INTRODUCTION - JACK VOLTAIC 3.0
- 4. JACK VOLTAIC RESEARCH METHODOLOGY
- 5. EXECUTION
- 6. FINDINGS
- 7. CONCLUSION
- APPENDIX A – ACRONYMS
- APPENDIX B – PARTNERS
- APPENDIX C – SCENARIO
- APPENDIX D – LAW/POLICY TABLETOP EXERCISE (TTX)
- APPENDIX E – LIVE-FIRE EXERCISE
- APPENDIX F – MILITARY TESTIMONIALS
- APPENDIX G – PRIVATE INDUSTRY TESTIMONIALS
- APPENDIX H – ALL HAZARDS ANALYSIS (AHA)
- APPENDIX I – CIRI FORT-TO-PORT DISRUPTION
- APPENDIX J – REQUIRED DELIVERY DATE (RDD) SIMULATION
- APPENDIX K – DSCA/DSCIR